Detecting Living off the Land Techniques

Long overlooked as a threat surface, many organizations have become increasingly concerned about their network infrastructure and attackers using these devices in combination with living off the land (LOTL) techniques to accomplish their various nefarious objectives: One of those actors, dubbed Salt Typhoon, made headlines earlier this year and brought this often neglected threat surface to the forefront in many peoples’ minds.
The Cisco Talos analysis of Salt Typhoon observed that the threat actors, often using valid stolen credentials, accessed core networking infrastructure in several instances and then used that infrastructure to collect a variety of information, leveraging LOTL techniques. Some of the recommendations to detect and/or protect your environments include:
- Monitor your environment for unusual changes in behavior or configuration.
- Profile (fingerprint via NetFlow and port scanning) network devices for a shift in surface view, including new ports opening/closing and traffic to/from (not traversing).
- Where possible, develop NetFlow visibility to identify unusual volumetric changes.
- Encrypt all monitoring and configuration traffic (SNMPv3, HTTPS, SSH, NETCONF, RESTCONF).
- Prevent and monitor for exposure of administrative or unusual interfaces (e.g., SNMP, SSH, HTTP(s)).
Below, we will examine how some of these monitoring and detection actions can be accomplished with Cisco Secure Network Analytics (SNA).
Network Threat Detection with Cisco Secure Network Analytics
Through the collection of network metadata, predominately NetFlow/IPFIX, Cisco SNA provides enterprise-wide network visibility and behavioral analytics to detect anomalies indicative of threat actor activity, such as the LOTL techniques used by some of these sophisticated threat actors. With a little tuning and some customization, the analytics and threat detections can be made to reliably identify threat actors misusing network equipment.
In tuning SNA for these types of detections, we’re going to do three major tasks:
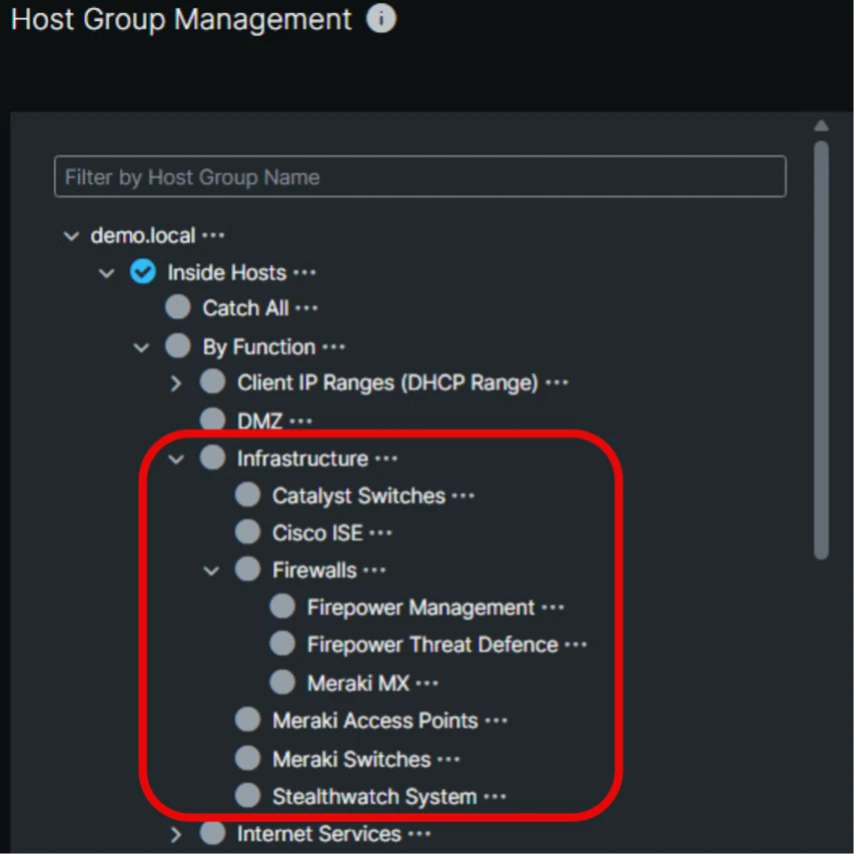
- Configure Host Groups for Infrastructure
- Create Custom Security Events and Role Policies
- Create a Network Diagram for Monitoring
1. Configure Host Groups for Infrastructure
- Define Host Groups in SNA to categorize your network infrastructure devices such as routers, switches, and jump hosts. This grouping allows focused monitoring and easier identification of suspicious communications involving critical infrastructure.

2. Create Custom Security Events and Role Policies
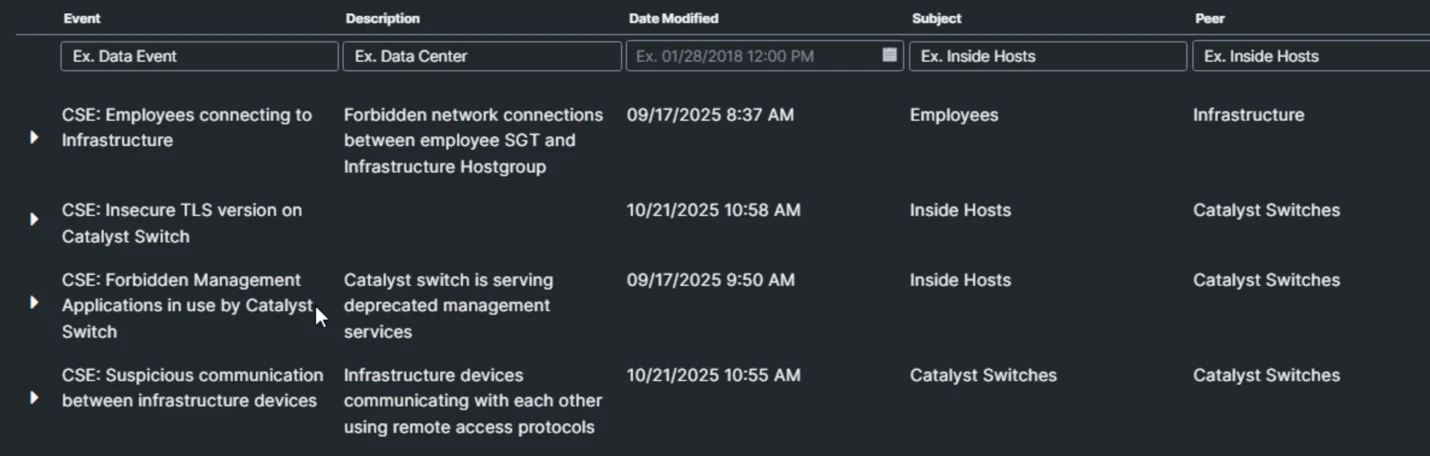
- Leverage threat intelligence from Cisco Talos, including indicators of compromise (IOCs) and behavioral patterns described in the Salt Typhoon analysis.
- Build Custom Security Events in SNA to detect suspicious or forbidden communications, such as unusual or forbidden traffic patterns. Examples include monitoring for employees connecting to the infrastructure host groups, the use of deprecated management protocols such as telnet and suspicious communication between network management planes (ex. SSH sessions between switches).

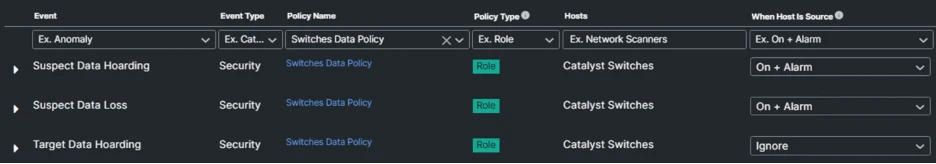
- Define Role Policies to further tune the core events to better detect suspicious and/or anomalous activity by switch management that may indicate lateral movement, data hoarding, and/or exfiltration.

3. Develop a Network Diagram for Monitoring
- Use SNA’s network diagram feature to create a network topology visualization to simulate a detailed diagram of your infrastructure hosts and their communication paths. This visual aid helps in quickly spotting anomalous lateral movements or unexpected data flows involving jump hosts or infrastructure devices.


Monitoring for Threat Actor Activity
Now that we’ve tooled some of the detection system, we begin active monitoring. Remember that at any time you can always go back and tweak the custom security events or adjust the alarm thresholds in the role policy to better monitor your environment. Ultimately, when monitoring for the LOTL activity expressed by these threat actors, we’re watching network management plane traffic and/or other (often unmonitored) infrastructure devices for suspicious and/or malicious seeming activity. It is always worth noting that your own security policy can have significant impact on what is determined to be suspicious and/or malicious.
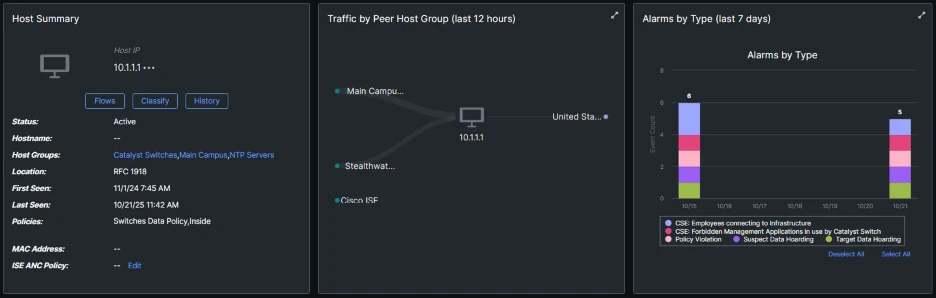
When Alarms occur, you can view them in the host page: in the example below, the host [10.1.1.1] belonging to the host group Catalyst Switches has expressed numerous policy violations: the custom security events above as well as Data Hoarding (collecting a lot of data from an internal system) and Target Data Hoarding (sending large amounts of data to another system), indicating that a malicious actor is remotely accessing this device and using its management plane to download and forward traffic.

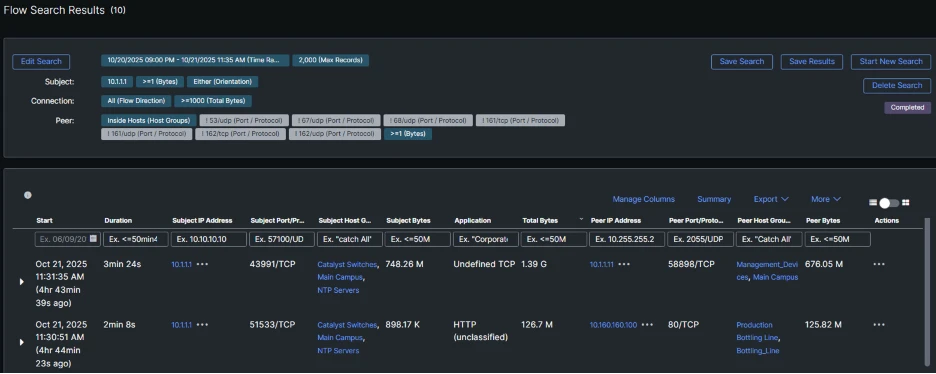
Digging into the flow records for the security events associated with the above switch confirms that it downloaded a large amount of data from the Bottling Line and uploaded it to an unmonitored management desktop.

Conclusion
With some clever tooling, Cisco SNA can be effectively used to monitor infrastructure and, through the analysis of network behavior analysis, detect sophisticated threat actors in the environment. Types of living of the land techniques SNA can be effective at detecting on infrastructure include:
- Unauthorized or suspicious logins to network devices.
- Suspicious lateral movement between infrastructure hosts.
- Data hoarding, forwarding and other unusual data flows.
- Data exfiltration attempts through unmonitored hosts in the network
Alerts generated by SNA are enriched with context such as user identity, device, location, and timestamps, enabling security teams to investigate and respond effectively.
To learn more about how Cisco SNA can help you detect advanced threats like Salt Typhoon and protect your network infrastructure, visit the Cisco Secure Network Analytics product page and explore demos and resources.
We’d love to hear what you think! Ask a question and stay connected with Cisco Security on social media.
Cisco Security Social Media